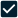
Access & Visitor Management For Changing Security Expectations

The most successful plans of this nature we’ve seen were created with input from traditional security and compliance professionals, internal policy-makers, legal counsel, HR teams to consider visitor management and facility access strategies and sponsors in environment, health and safety (EHS) branches.
Balancing input is the key to success, at least in this planning phase.
Security screening is a perfect example: It needs to follow Health Canada and provincial regulations, but legal considerations must also be accounted for as this process crosses into data privacy, employee rights and the Federal Labour Standards of Canada. Additionally, HR and PR may each have something to say about what kinds of screening can and should be considered, based on how intrusive they might be.
For these reasons, no company should rush to implement an access management strategy. They should act smartly, from an informed place, and with the best interests of everyone who walks through the environment (staff and visitors).
The New Tech Rush in Visitor Management & Access Control Technologies
Businesses are looking for new solutions to improve security screening and introduce long-term strategies to protect employees and guests from COVID-19, and technology is stepping up with innovations like surveillance cameras with advanced video analytics that let companies count and contact-trace people in their environments.
It’s exciting stuff, and it’s easy to get blinded by the marvel of what some of these technologies can do. However, it’s important for businesses to implement innovative solutions responsibly. This means understanding each technology option, what it can and can’t do, how to use it effectively and ethically, and what (if any) effect it will have on employees. It means leaning more towards technologies with proven reliability and efficacy. And when you do find one worth exploring more, it’s worth considering:
- How well does it fit into your existing strategies, plans and facilities?
- Who is going to be responsible for this system and at what cost?
- How will you organize, analyze and benefit from the data it will generate?
Barriers to Improving Visitors Security Screening
The rapid adoption of security screening shone a light on the pre-existing challenges of implementing this kind of technology. Two of the more significant challenges that are slowing down post-COVID implementation of security screening are silos within organizations and inefficient data management — as both create potentially dangerous information gaps.
Another set of barriers includes outdated visitor registration and credential checking. Both create an unnecessarily time-consuming process of trying to admit customers, contractors, vendors and visitors. It’s a struggle to improve access management with technology when it’s currently built on physical security guards and paper-pushing.
By updating the core of these processes, rather than simply placing new systems on top, an organization will improve its information-gathering ability, reduce the number of touchpoints and encourage compliance.
Our Visitor Management Solution
Your visitor management solution will take data, privacy, and compliance into account while strengthening your overall safety strategy.
Our approach to physical identity and access management (PIAM) includes practical technologies, customized for your existing systems to avoid having to tear out or rebuild your existing architecture.
One is a flexible middleware solution that reduces touchpoints and speeds up check-in by automating key processes like security screening for employees, visitor management and credential verification.
Another is an access management solution that can help coordinate your physical and logical security protocols, improve information flow across previously closed-off sections of your business and maintain compliance.
If you’re interested in learning how to integrate a PIAM system, fill out a form to obtain a free personalized quote.
Disclaimer: By using the Blog section of this website (“Blog”), you agree to the terms of this Disclaimer, including but not limited to our terms of use and our privacy policy. The information provided on this Blog is for informational purposes only. Such information is not intended to provide advice on your specific security needs nor to provide legal advice. If you would like to speak to a security representative about your specific security needs, please contact us.